Companion Surveillance and Surveillant Subjectivities: On the Seduction of Seeing and Being Seen
 Monday, March 21, 2016 at 9:36PM
Monday, March 21, 2016 at 9:36PM Gavin J.D. Smith
[ PDF Version ]
“I do not want to live in a world where everything I do and say is recorded.” - Edward Snowden[1]
Edward Snowden’s 2013 disclosures were among the most significant leaks of classified intelligence information that the world has seen. Snowden’s revelations unveiled how the actions of unknowing individuals were subjected to mass tracking by an overlaying surveillance matrix. His insights put the issues of surveillance excess, democratic process, and civil rights on the public, political, and judicial radars. They accentuated the significance of surveillance measures in establishing power asymmetries and determining the life-chances of citizens. They showed the complicity of Internet service providers in the unlawful sharing of users’ personal information with security and intelligence agencies. They highlighted the intricate data exhaust that citizens routinely emit from their bodies as they participate in daily activities, and how this outflow is routinely mined and profiled against risk indicators. They painted a portrait of state-corporate collusion in surveillance operations and informational exchange. They illustrated the intimate relationship between surveillance practices, processes of capitalism, and the flexing of sovereign power.
But how has the global mediatization of these disclosures been popularly received? What types of resonances have they had in terms of public understandings of surveillance and public (dis)trust in state agencies and corporate enterprises? More specifically, has this knowledge altered public behavior in regard to data sharing? My argument is that little has changed if we consider the depth of media embedment in cultural life. If anything, individuals are participating in their own regimes of self-exposure via data sharing at an increasing rate. Although the issue of mass indiscriminate surveillance has gained much traction in policy and diplomatic circles and received extensive global media coverage, there has been no organized and sustained public backlash. No notable revolution has occurred in how people approach and manage their daily visibility, and what demands they place on public and private organizations as custodians of their personal data. While not denying the existence of individualized acts of resistance to surveillance tracking,[2] it is debatable how widespread or collective these practices are and whether they pose any significant interruption to the growing capacity and dominance of networked surveillance systems. Despite the emergence of prominent ephemeral initiatives such as “Reset the Net” and “Stop Watching Us,”[3] few, if any, anti-surveillance demonstrations and campaigns have materialized as enduring oppositional forces that exert leverage over regulatory legislation and legal codes. There has been a scarcity of boycotts of online media platforms, search engines, and digital devices and apps. Indeed, people are creating and exuding more data than ever before and the profits of IT companies are expanding rather than diminishing. For example, tech firm Cisco recently estimated that an equivalent to 650,000 DVDs worth of data transited the United Kingdom every hour in 2014, and that mobile data emissions will grow by 57% from 2014 to 2019.[4] These are not signs of a surveillance infrastructure and economy in crisis: anything but.
So, how might we make sense of the apathetic response to Snowden’s whistleblowing in most countries—especially given that they accentuated state and corporate incursions on key constitutional and human rights? From a different angle, which factors explain continued public obedience to the mass surveillance of their bodies and personal lives? Addressing these questions necessitates that we consider the subjective meanings that individuals ascribe to the experience of visibility: how being exposed via data emissions makes them think, feel, and act. This entails adopting Michel Foucault’s notion of visibility as normative—as establishing specific habits, practices, and relations[5]—but also incorporating Judith Butler’s characterization of visibility as performative—as a relational frame through which identities are exhibited and attributed.[6] These frameworks, I suggest, offer a means to rationalize the relative absence of collective and transnational action in the aftermath of Snowden’s disclosures. I wish to show how a generalized subjectivity that is congenial to repertoires of watching and being watched (that is normative and performative) has emerged as an outcome of processes of socialization that have materialized in organizational and cultural fields. Each field of practice has, for different reasons, naturalized the practice of data sharing and the desirability of visibility, and has programmed the mindsets of agents to develop an uncritical and indifferent relationship to their personal data. The upshot is that networked media technologies and infrastructures are so deeply engrained in the fabric of daily life as “companion structures,” and individuals are so thoroughly habituated in the viewing and sharing of personal data and becoming with this medium, that any form of mass collective action to delegitimize and prohibit processes of bulk data scraping and mining by states and corporations seems improbable.
I. The Normalization of Visibility
Theorizing Visibility
“Disciplinary power . . . is exercised through its invisibility; at the same time it imposes on those whom it subjects a principle of compulsory visibility. . . . Their visibility assures the hold of the power that is exercised over them. It is the fact of being constantly seen, of being able always to be seen, that maintains the disciplined individual in his subjection.” - Michel Foucault[7]
Foucault’s seminal analysis of the visibility produced through the spatial architecture of the panoptic prison accentuated the normalizing properties of this condition—its capacity to establish particular perceptions, behaviors, and power relations. It drew attention to the unseen and constitutive properties of disciplinary power, which is exercised via subjects’ exposure to a gaze that penetrates—and reforms—their minds and souls. Being rendered visible for Foucault was tantamount to a trap, a way of being subjugated by the inspective scrutiny of an external authority figure. Power flows through the medium of the gaze and the resultant sensation the object feels of being on display—of needing to manage impressions and present the appropriate façade. Although many scholars have problematized Foucault’s overly hierarchical and deterministic depiction of visibility, especially in terms of how it is experienced in practice as a relational process,[8] there is value in retaining this hermeneutic for its capacity to elucidate the cultural fascinations with watching and being watched. It sheds important explanatory light on the apparent public apathy toward Snowden’s cautionary disclosures in terms of behavioral inertia. Foucault’s contention that visibility exerts normalizing effects on those watching and those being watched situates it as a mode of governmentality, as a technique that produces asymmetrical power relations and the performance of desired behaviors. That is to say, technologies of visibility create conditions of visibility, which, in turn, engineer “subjectivities of visibility.” These subjectivities are defined by a dual penchant to spectate and to reveal, to be a subject and agent of surveillant spectacles. The fact that technologies of visibility are so ubiquitous in the modern world has revolutionized what and who is seen and thus, what individuals are willing—and expected—to share about themselves and others.
Judith Butler’s account of how gender is ritualistically performed (and culturally contingent) accentuates the centrality of presenter, audience, gaze, act, and script in the mutual co-construction of selfhood.[9] For Butler, gender is not an essentialist or fixed state, but a fluid and relativistic social construct that is symbolically enacted and reified in the course of everyday relations. These relations reflect particular heteronormative codes and hegemonic claims and present them as natural and indisputable. Gender becomes a medium through which patriarchal values are upheld and reproductive interests are serviced. As she observes, “[G]ender is in no way a stable identity or locus of agency from which various acts procee[d]; rather, it is an identity tenuously constituted in time—an identity instituted through a stylized repetition of acts . . . , a constructed identity, a performative accomplishment which the mundane social audience, including the actors themselves, come to believe and to perform in the mode of belief.”[10] This notion of subjectivity as being relationally co-constructed through the performance of roles, including stylized presentations of self and audience participation and reaction, is helpful for understanding how visibility operates and what effects it leverages. Namely, being the point of a gaze and the subject of a reflection—specifically one that is electronically mediated—enables modes of distanced interactivity to occur between performer and audience that pivot on identity work. The concept of performativity lets us appreciate the seductive and relational dimensions of seeing and being seen, and it accentuates that visibility, for both watcher and watched, can be as much a source of pleasure as a means of vulnerability and subjugation. But it equally allows us to perceive the complex, networked, and quantum character of contemporary visibility. Locally staged performances are now instantaneously decontextualized and subject to the pluralistic gaze of third-party observers who may codify the data in ways the performer had not intended. Performances of self in the digital age reach much broader audiences than ever before, but the effects these presentational acts have on networked audiences separated in time and space are becoming harder to anticipate. For instance, a flippant tweet or Facebook comment made in the context of an evening out with friends can result in a person receiving unwanted advertisements, being harassed, or losing her job (see Figure 1).
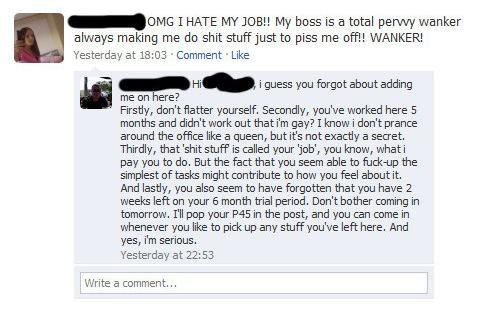
Figure 1. A networked Facebook comment that resulted in the poster being dismissed from her job. Source: Business Insider.
Therefore, visibility acts as an instrument of both self-governance and self-expression. It is a nexus point for competing forms of control, creativity, and community. It is a core medium through which subjectivity is constructed and performatively staged. Identity is thus closely bound up with practices of seeing and being seen, with visibility mediating meanings of the self—in terms of what we project and how we introspect. The diverse functions of visibility, and its embedment in the structure of social relations, helps elucidate why many have done little to alter their data sharing habits. Being hardwired into a conventional form of practice takes time, effort, dedication, and resolution to unravel.
Escalating Visibility
“The coalescence of [data traces and points] into the surveillant assemblage marks the progressive “disappearance of disappearance”—a process whereby it is increasingly difficult for individuals to maintain their anonymity, or to escape the monitoring of social institutions.” - Kevin D. Haggerty and Richard V. Ericson[11]
A diverse array of networked media technologies now datafy and track bodies as they participate in everyday activities. CCTV camera networks, credit and loyalty cards, body scanners, smartphones, social media platforms, Fitbits, and browser cookies constitute only some of the many extractive mediums that routinely capture and circulate data flows. Many of these devices embody the correlated modern rationalities of “action at a distance”[12] and “government at a distance.”[13] Multiplex sensors embedded in the networked smartphone continuously monitor daily habits. These responsive sensors connect to applications that register and analyze sleep patterns, mood, sexual experiences, and consumption preferences. Each data sequence they generate is permanently recorded and immediately displayable as a graphic visualization, as a means for datafied subjects to track, measure, and compare their bodily performances. As a core currency of informational or knowing capitalism, data flows are incessantly moving to and from nodal monitoring stations where they are recalibrated as “derivatives.” As Louise Amoore explains, “The data derivative comes into being from an amalgam of disaggregated data – reaggregated via mobile algorithm-based association rules and visualized in “real time” as risk map, score or colour-coded flag.”[14] The derivative is the register through which networked audiences risk profile ‘dividuals’—i.e. subjects distributed in aggregates as electronic signatures—as normal or abnormal, valuable or expendable.[15]
Processes of datafication have significantly increased in recent times. For example, according to IBM, 2.5 exabytes (2.5 billion gigabytes) of data were generated every day in 2012.[16] Google now records more than 3 billion search queries and processes 24 petabytes of data daily.[17] Facebook has over 936 million active users that generate 2.7 billion “Like” actions and 300 million photos per day.[18] Viktor Mayer-Schönberger and Kenneth Cukier note that the social graph Facebook produces “represents more than 10 percent of the total world population, datafied and available to a single company.”[19] The average UK adult has personal information registered on approximately 700 separate databases.[20] The Library of Congress claims its archive of public Twitter messages has reached 170 billion tweets.[21] Walmart holds 460 terabytes of consumer data[22] and Tesco holds two years of purchasing data for 16 million households, which equates to the consumption habits of 40% of the UK population.[23]
Organizations primarily use data for actuarial ends, to minimize risks and to maximize returns. Converting behaviors into visualizations helps them anticipate market trends, coordinate logistics, develop interventions, and optimize services. Probabilistic simulations inform decision-making and assist administrators in preparing for future scenarios. The data-industrial complex is powered by political, economic, social, and cultural imperatives that include desires to mine troves of data for insight, and desires to accrete self-understanding, self-validation, and social status from sharing personal data. The search for behavioral standards and deviations propels—and justifies—the erection of more systems of oversight to monitor bodily conduct. As the amount of data increases, new problems arise that require additional data to solve. A primary effect of coalescent datafication is the progressive “disappearance of disappearance” as formerly discrete systems of monitoring increasingly converge their data stockpiles. The proliferation of mobile tracking devices and the intersectionality of data points have cultivated a situation in which contemporary individuals (whom I call “technovisuals,” to reflect their deep entanglement with visualizing technologies)[24] experience declining prospects to disengage from the bordering “surveillant assemblage,”[25] which shrouds moving “data targets” in representational fields of visibility.
Having outlined the normalizing nature and performative effects of visibility, I will now demonstrate how a range of related dynamics in organizational and cultural ecologies cultivate a subjectivity that is habituated into acts of spectating and revealing. This disposition is the outcome of technologies and interests that jointly produce the condition of networked visibility. But it also contributes to the market demand for such visibility-producing infrastructures. It is conditioned to perceive visibility as normal and desirable which helps explain the comparative lack of continuing indignation in the fallout of Snowden’s salient intervention.
II. Habituation and Seduction
Bureaucratic Procedures and Organizational Requirements
One of the main factors that accounts for the naturalization of surveillance technologies and processes is the bureaucratic need to collect detailed records, classify phenomena, and audit the efficacy of services. As Max Weber noted, bureaucracies operate in accordance with rational-legal principles, and their authority is contingent on extensive trails of documentation. This knowledge enables officials to establish expertise, instrumentalize decision-making, and optimize administrative procedures. The bureaucratic system emerged with modernity in a context of increasing societal complexity, fluidity, and uncertainty. As a mode of social organization, it is built on an intricate technical infrastructure that can individuate and authenticate its clientele from a distance. Participation in modern society entails interfacing with multiple organizations that espouse these logics and practices. The historical emergence of the bureaucracy has entailed a process of making individuals visible in order to administer services effectively and dispassionately.
The archetypal medium of the bureaucracy is the administrative record, which incorporates the personal circumstances of each client over time. An obvious example of this is the patient medical file. A key outcome of bureaucratic practice is that individuals are habituated into performing repertoires of identification. From the classroom to the workplace, subjects are instructed to routinely produce identifiers and have their personal details registered. To attain legitimacy and normalcy, this process of supplying evidence to corroborate both a personalized and bureaucratic story has been executed under the rubrics of impartiality, transparency, and efficacy. The modern organization prescribes that its employees and customers’ activities be highly visible in return for the provision of welfare, wages, and security. The airport terminal provides a illustration of this modality as a lived, embodied practice. Passengers must consent to a multitude of intrusive security checks before they are permitted to transit, from submitting personal details for screening in advance to showing identification to having their bodies scanned. Cumulatively, these organizational repertoires develop individuals’ conversancy with being involuntarily watched and instill the perception, via discourse and signage, that monitory attention is a custom that serves their interests and other progressive ends. One trades anonymity and invisibility for access to automobility, social media networking, state services, and consumer protection. Because this instruction occurs systematically from birth to death, becoming especially pronounced during an individual’s formative years in the educational system,[26] it is nigh impossible for citizens to envisage alternative futures and structures that relations of visibility do not deeply permeate.
In this way, individuals are institutionally conditioned to reveal personal information. This practice becomes part of a bureaucratically created habitus within a broader field of administrative visibility. Time-poor individuals are seduced by the convenience of trading their data for quicker responses and customized products. They share information with third-party operators to avoid duplicating cumbersome data entry protocols or navigating obtuse privacy policies. Invisibility-reducing settings are deliberately designed as the default on many online platforms. It takes time, proficiency, and resources—that is, the investment of labor—to maintain an incognito presence online. This is particularly the case with the recent introduction of privacy-reducing data retention laws in many countries. Being seen has become an organizational norm that is dressed up in the guise of procedural rationality and accountability.
Paternalism, Insecurity, and Ignorance
In addition to the contemporary routinization of visibility rituals, powerful discourses also rationalize the deployment of surveillance technologies and systems. Political actors accentuate the overwhelming diversity of threats, including crime, terrorism, natural disasters, and infectious diseases, that confront citizens. Because glocal events are now mediated spectacles for globally connected audiences, they give rise to a cosmopolitan consciousness that is imbued with a concern about the stability of the social world. Governmental narratives dramatize the dangers of not installing surveillance dispositifs or not legislating greater state powers, and they justify these measures on the grounds of escalating conditions of risk and uncertainty. The proliferation of CCTV camera networks in the 1980s and 1990s in many developed nations exemplifies this process.[27] Taxpayers and consumers expended huge sums of money on these so-called “silver bullet” techno-panaceas in response to rising concerns about public safety. In the UK, the public was inundated with partisan rhetoric that emphasized the astonishing effectiveness of CCTV. A surge of high-profile CCTV images on television and in newspapers further indicated the reality of urban fragmentation and the need for a technical intervention in a space where social welfare policies had apparently failed. With little more than a shred of evaluative evidence to demonstrate that the cameras actually reduced crime and made the public feel safer, an impulsive UK government invested over three-quarters of its crime prevention budget on the installation of thousands of cameras nationwide. The incessant lobbying of ministers, police officers, business executives, councilors, and journalists paid off: public opinion was turned in favor of the technology, and a historic process of civic surveillance and the transformation of the public sphere was initiated with limited resistance.

Figure 2. A sign from the Metropolitan Police’s counterterrorism campaign.
These risk discourses and security tropes appear in many contexts. As paternalistic governmentalities and manipulative rhetorics, they seek to exploit the anxieties of subjects and compel them to develop susceptive attitudes and perform stipulated behaviors. Spaces and objects are subsequently redefined, based on their perceived level of risk. A population of fearful subjects is also responsibilized to uncritically conform with intrusive surveillance practices and report 'suspicious' individuals, practices, and events. The US Department of Homeland Security’s recent “If you see something, say something” campaign[28] or the 2009 Texas Virtual Border Watch program, which incentivized the public to remotely monitor security cameras positioned along the US-Mexican border and spot illegal migration attempts,[29] exemplify how the state frames risk work as a civic duty and mobilizes citizens to perform security tasks. Key to ensuring that sufficient numbers acquiesce to declining civil liberties and intensifying security measures is the tight control of information dissemination. Uncertainty is deliberately manufactured around threats. A nationalistic “us vs. them” sentiment is also established, producing a binary that only exacerbates pre-existing racial and ethnic antagonisms. In addition, the state exploits prominent, albeit isolated, events to pass exceptional bills and heighten police powers while civil society is reeling in a state of shock and outrage. Two such instances are the US Patriot Act that followed in the immediate aftermath of the September 11 attacks, and the sweeping data retention laws the Australian government introduced after the 2014 Lindt café siege in Sydney. The state’s use of “agnotology”—willfully making its population ignorant about the nature of problems to present cost-effective technical solutions that unevenly benefit state and market actors—is designed to manufacture obedience and limit dissent.[30] Most members of the public choose to ignore the details of how and why their data are continuously harvested by extractive media devices and infrastructures. They only become cognizant of the transformative significance of data sharing and mining practices after they generate a negative consequence.
To justify its increased presence in citizens’ personal lives, the state strategically evokes the maxim, “If you have nothing to hide, you have nothing to fear.” This proverb vindicates the notion that enhanced surveillance is for the public good by intimating that it is exclusively deployed against targets that harbor malign intent. It contradicts the narratives of those who perceive privacy and secrecy as healthy aspects of a democracy. This attitude stimulates a culture of confession in which individuals are expected to willingly reveal truths about themselves and others, and live within ecologies of visibility. It assumes that authorities are capable of equitably processing data and are not susceptible to the vagaries of personal impulses. Yet, many historical examples demonstrate the utter fallibility of these assumptions.[31]
Connectivity and Performativity
The routinization of data sharing behaviors does not only pervade the organizational field. The cultural field is another key vector that institutes blasé attitudes toward personal information and develops the seductions of seeing and being seen. People use participatory surveillance media like Facebook, Instagram, and Twitter to voluntarily disseminate personal impressions to networked audiences and to consume other users’ data. These platforms link nodal individuals to spatially dispersed virtual networks, and they act as conduits for expressions of feelings, opinions, and identity that are dutifully crafted in accordance with emerging “networked socialities.”[32] Moreover, they provide a means of actualizing everyday desires and producing and consuming (or “prosuming”) personal content. Individuals become both “surveillance agents” and “surveilled subjects” in their interactions with these mediums. As tools of empowerment, they can be appropriated to derive social meanings from sharing virtually intimate relations with others, to experiment with and project variable presentations of the self, and to fix identity to particular issue-driven communities. Media infrastructures also provide a relational lens through which embodied experiences and attitudinal opinions can be contrasted. The significant social value of networked cultural practices helps explain the reluctance of many to adjust their use of media devices and reduce their digital footprint.
The cultural premium placed on the production, sharing, and consumption of data has hardwired people into a habitus where networked digital technologies become “companion structures” in the weave of social relations.[33] People progressively become with data and use these media for experiences of pleasure and meaning-making. The cult of celebrity that shapes the cultural landscapes of many advanced capitalist societies further naturalizes the desire to be on permanent display. As Robert van Krieken has persuasively argued, an “economics of attention,” or the ability to captivate the gaze of fickle audiences, has become important social currency in an age of celebritization.[34] Sharing gossip, receiving validating feedback, and being seen in enviable social situations are desirable attributes in a 24/7 newsfeed economy. Individuals receive the esteem of peers and corporate rewards for broadcasting their sentiments and whereabouts, and for managing a performative networked self. They simultaneously derive voyeuristic titillation from tracking the social experiences of others. As the extraordinary success of reality television indicates, there is a cultural fascination with performativity, intimacy, and watching anonymously. This also rationalizes the ambivalent public response to state-sanctioned mass monitoring.
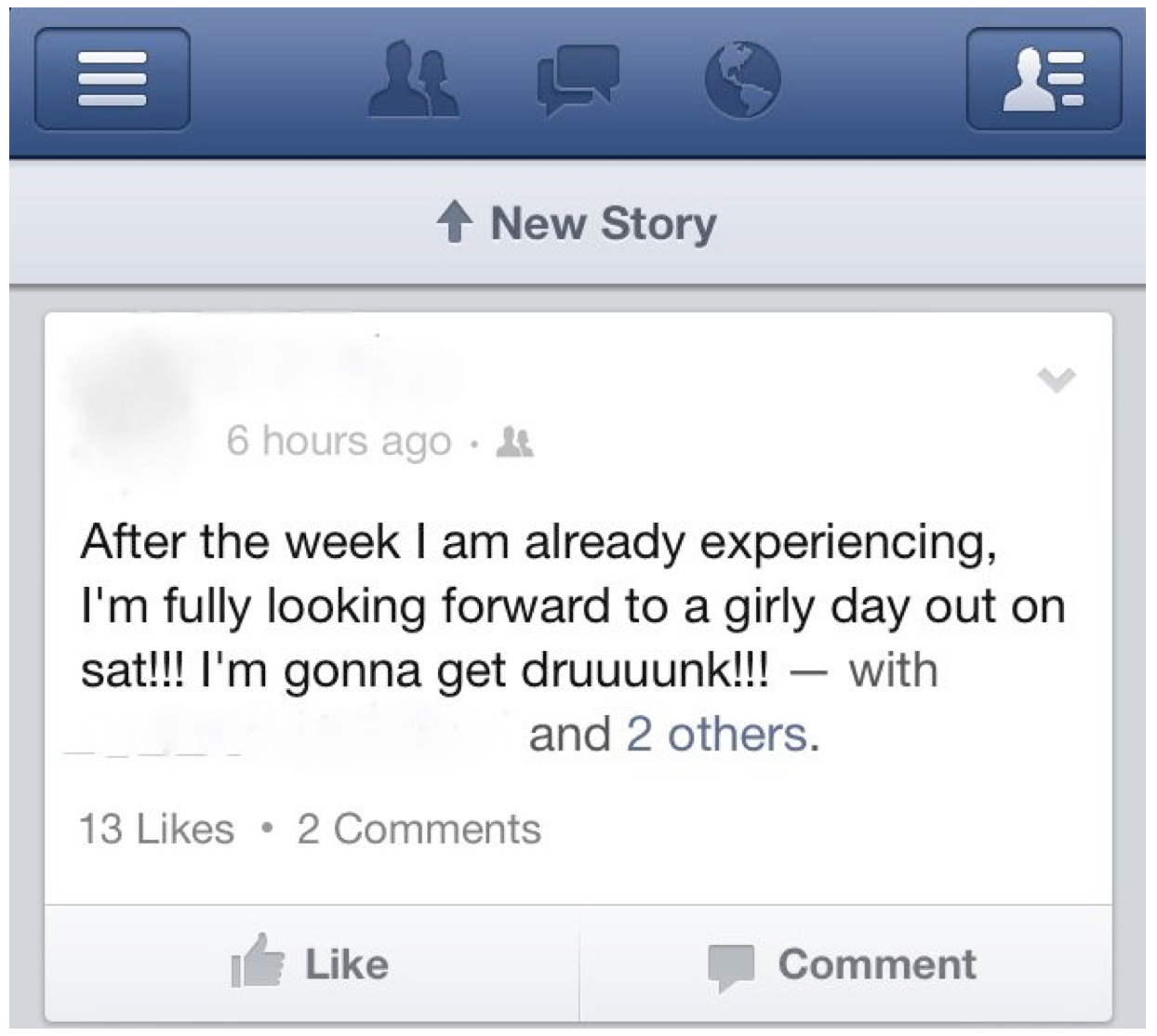
Figure 3. An anonymized Facebook share that illustrates how personal outlooks are increasingly projected onto public forums to garner “attention capital” from networked audiences.
Developments in the capabilities of sensor/sensing technologies facilitate the appearance of previously latent behaviors. The miniaturization and digitalization of the camera, now embedded in the smartphone as a standard feature, is key to this change. Bodily intimacies, from sexual conduct to health status, are increasingly rendered as mediated spectacles and as objects of fascination for anonymous televoyeurs dispersed in space-time. Browsing YouTube shows that key life events, from births to autopsies, are readily accessible for viewing via an Internet-enabled device. Being privy to mediated spectacles exposing the human condition in its various guises inspires mimicry in many and compels the production of progressively more videos that feature personal stories. Watching the intimate lives of others unfold through the ontological barrier of the screen mediates how technovisuals experience their bodies, relate to those around them, and selectively exteriorize aspects of their own interiorities.
The extraordinary success of CCTV is one case in point. Viewers of CCTV images can converge time-space discontinuances and watch events develop in granular detail. The sequences they watch telecast the extremities of modern lifestyles and stimulate experience-driven audiences. They provide opportunities to indulge in fantasy and reflexivity. In large part, the cultural acceptance—and spectacular success—of CCTV is a result of its capability to transmit both the ordinary and the peculiar. CCTV imagery incorporates textual realism and provides additional lenses—and bionic resources—through which spectators can revel in distant events as “absent witnesses.”[35] One example is the unlawful release (and subsequent virality) of security footage that depicts a shopper accidentally plunging into a mall fountain while texting on her mobile phone (see Figure 4).[36] As “harbingers of truth” and “vectors of subjectivation,” CCTV films are implicated in verity claims and become the objects of a scopophilic gaze.[37] Displaying the egregious, exalting, and frivolous, they regularly appear as storytelling mediums and moral referents in entertainment shows and on websites.[38] They inform our appreciation of how people live and, often, how people ought not to live. The intimate but indirect simulacra that portray the human condition in its vapidity, majesty, and cruelty function as a modern form of cave painting. They enable the intergenerational relay of parables via the medium of images and the anonymity of the screen. As performative media, surveillance systems produce visual texts that are both the cause and consequence of a viewer culture.

Figure 4. The now-viral sequence that shows a woman falling into a fountain while texting on her smartphone. Source: We Interrupt.
Conclusion
This essay has sought to explicate the lack of public resistance to surveillance technologies and processes in the wake of Edward Snowden’s 2013 disclosures. Although a growing interdisciplinary literature considers how surveillance processes affect the character and experience of everyday life, limited research focuses on the dimension of culture. Cultural factors can help explain why monitoring and data gathering practices have such appeal, have become so deeply embedded in the architecture of the mind, body, and soul, and thereby, are so inconspicuous as they operate in/on physical and social spaces. The analyses that do exist tend to explain the naturalization and normalization of surveillance by pointing to either state authoritarianism and/or deliberate state and corporate indoctrination of the masses. But I have suggested here that the situation is more complex. It is less the outcome of a top-down plot and more the disorganized product of “relations of visibility,” in terms of our embedment within a organizational and cultural field that venerates the visual and promotes the acts of seeing and being seen. Data, the key medium and reflector of visibility, is just too deeply entangled in everyday practices and impressions/expressions of identity, as well as in claims to knowledge, for a revolutionary moment to materialize when data-based socialities are abandoned. I have proposed that the ontological aspects of visibility, its normalizing and performative properties, account for its prevalence and our attachment to it. Hence, today’s technovisuals generally cannot imagine an alternative data-free life: an existence without connectivity and data-driven interactivity.
Part of this has to do with semantics and knowledge. Not all technovisuals understand that media devices double as surveillant probes, nor do they understand how, when, and why their data are harvested and by whom. But a further aspect concerns how organizational and cultural practices simultaneously socialize people into the belief that data-driven visibility is necessary, inevitable, and desirable. I have argued that making sense of the scant opposition to mass data-based tracking entails considering how visibility as a social condition becomes a surveillant subjectivity that orients behavior. This subjectivity is defined by a dual penchant to spectate and to reveal.
The culture of visibility that companion surveillance and surveillant subjectivities facilitate jeopardizes values like the freedom of expression, the capacity to be alone, and the ability to unplug from an overarching surveillant matrix. The punctuation of visibility into backstage regions has the potential to rouse “performativity fatigue syndrome.” This concept refers to a condition endured by social actors who, partly through their own choices but partly as a product of system design, can no longer preserve voluntary invisibility or retain autonomy and ownership over their self-presentations. This inability to control data flows has the capacity to induce feelings of alienation, anger, shame, and anxiety. Moreover, the declining number of “free spaces” (i.e. places and moments where data is not being emitted from the body) in which subjects can experiment with identity, commit transgressive acts, or make mistakes without concern of being recorded might inhibit the accomplishment of existential objectives, of being able to learn from and then forget social errors like inadvertently falling into a shopping mall fountain. Instead, networked audiences have now privileged access to datafied versions of the self, which are durable and circulative in format. The emergence of these data transfers presents new challenges for technovisuals, because the information they voluntarily and involuntarily share influences how audiences initially codify them and the treatment they receive prior to direct contact. The introduction of the No Fly List in the US, which saw innocent individuals banned from air travel due to their assigned risk rating, provides an extreme, if poignant, example of how the performativity of disembodied data may soon supplant the performativity of the embodied subject.
Notes
[1] National Security Agency, “Edward Snowden,” National Security Archive; Ewen MacAskill, “Edward Snowden, NSA files source: “If they Want to Get You, in Time they Will,”” The Guardian, Jun. 10, 2013, http://www.theguardian.com/world/2013/jun/09/nsa-whistleblower-edward-snowden-why.
[2] See Gary T. Marx, “A Tack in the Shoe: Neutralizing and Resisting the New Surveillance,” Journal of Social Issues 59, no. 2 (2003): 369–390; John Gilliom and Torin Monahan, “Everyday Resistance” in Routledge Handbook of Surveillance Studies, eds. Kirstie Ball, Kevin D. Haggerty, and David Lyon (New York and London: Routledge, 2012), 405–411; and Torin Monahan, “The Right to Hide? Anti-Surveillance Camouflage and the Aestheticization of Resistance,” Communication and Critical/Cultural Studies 12, no. 2 (2015): 159–178.
[3] See Reset the Net, http://www.resetthenet.org and Stop Watching Us, http://rally.stopwatching.us.
[4] Cisco Visual Networking Index: Forecast and Methodology, 2014–2019 White Paper, Cisco, May 27, 2015, http://www.cisco.com/c/en/us/solutions/collateral/service-provider/ip-ngn-ip-next-generation-network/white_paper_c11-481360.html.
[5] See Michel Foucault, Discipline and Punish: The Birth of the Prison, trans. Alan Sheridan (1977; New York: Vintage Books, 1995).
[6] See Judith Butler, “Performative Acts and Gender Constitution: An Essay in Phenomenology and Feminist Theory,” Theatre Journal 40, no. 4 (1988): 519–531 and Judith Butler, Gender Trouble: On the Subversion of Feminism (New York and London: Routledge, 1990).
[7] Foucault, Discipline and Punish, 187.
[8] See Derek Kerr, “Beheading the King and Enthroning the Market: A Critique of Foucauldian Governmentality,” Science & Society 63, no. 2 (1999): 173–203; Majid Yar, “Panoptic power and the pathologisation of vision: critical reflections on the Foucauldian thesis,” Surveillance & Society 1, no. 3 (2003): 254–271; Hille Koskela, “Webcams, TV shows and mobile phones: empowering exhibitionism,” Surveillance & Society 2, no. 2–3 (2004): 199–215; Hille Koskela, “‘The other side of surveillance’: webcams, power and agency,” in Theorizing Surveillance: The Panopticon and Beyond, ed. David Lyon (Devon, UK and Portland, OR: Willan Publishing, 2006), 163-181; and Gavin J.D. Smith, Opening the Black Box: The Work of Watching (New York: Routledge, 2015).
[9] See Butler, “Performative Acts and Gender Constitution” and Gender Trouble.
[10] Butler, “Performative Acts and Gender Constitution,” 519–520. Emphasis in original.
[11] Kevin D. Haggerty and Richard V. Ericson, “The Surveillant Assemblage,” British Journal of Sociology 51, no. 4 (2000): 605–622, 619.
[12] Bruno Latour, Science in Action: How to Follow Scientists and Engineers Through Society (Cambridge, MA: Harvard University Press, 1987), 219.
[13] Peter Miller and Nikolas Rose, “Governing economic life,” Economy and Society, 19, no. 1 (1990): 1-31, 9.
[14] Louise Amoore, “Data Derivatives: On the Emergence of a Security Risk Calculus for Our Times,” Theory, Culture & Society 28, no. 6 (2011): 24-43, 27.
[15] Gilles Deleuze, Negotiations 1972–1990, trans. Martin Joughin (1990; New York: Columbia University Press, 1995).
[16] Matthew Wall, “Big Data: Are you ready for blast-off?,” BBC News, Mar. 4, 2014, http://www.bbc.com/news/business-26383058.
[17] Steven Levy, “Google Throws Open Doors to Its Top-Secret Data Center,” Wired, Oct. 17, 2012, http://www.wired.com/2012/10/ff-inside-google-data-center.
[18] “The Top 20 Valuable Facebook Statistics,” Zephoria, 2015, https://zephoria.com/top-15-valuable-facebook-statistics.
[19] Viktor Mayer-Schönberger and Kenneth Cukier, Big Data: A Revolution That Will Transform How We Live, Work, and Think (New York: Mariner Books, 2014), 92.
[20] “Trust warning over personal data,” BBC News, July 13, 2006, http://news.bbc.co.uk/2/hi/uk_politics/5172890.stm.
[21] Erin Allen, “Update on the Twitter Archive at the Library of Congress,” Library of Congress, Jan. 4, 2013, https://blogs.loc.gov/loc/2013/01/update-on-the-twitter-archive-at-the-library-of-congress.
[22] Constance L. Hays, “What Wal-Mart Knows About Customers’ Habits,” New York Times, Nov. 14, 2004, http://www.nytimes.com/2004/11/14/business/yourmoney/what-walmart-knows-about-customers-habits.html?_r=0.
[23] Sam Chambers, “The One Thing Tesco’s Big Data Algorithm Never Predicted,” Bloomberg, Oct. 21, 2015, http://www.bloomberg.com/news/articles/2015-10-21/tesco-s-prophecy-proves-costly-as-sale-of-dunnhumby-falls-flat.
[24] Gavin J.D. Smith, “Surveillance, Data and Embodiment: On the Work of Being Watched,” Body & Society, DOI: 10.1177/1357034X15623622, 3.
[25] Haggerty and Ericson.
[26] Torin Monahan and R.D. Torres, Schools under Surveillance: Cultures of Control in Public Education (New Brunswick, NJ: Rutgers University Press, 2010).
[27] See Smith, Opening the Black Box.
[28] See “If You See Something Say Something,” Department of Homeland Security, http://www.dhs.gov/see-something-say-something.
[29] See Richard Luscombe, “Patrol Watches Texas-Mexico Border - from Pub in Australia,” Guardian, Mar. 22, 2009, http://www.theguardian.com/world/2009/mar/23/texas-mexico-patrol-webcam-australia.
[30] Robert N. Proctor and Londa Schiebinger, eds., Agnotology: The Making and Unmaking of Ignorance (Stanford, CA: Stanford University Press, 2008).
[31] See Martin French and Gavin J.D. Smith, “Surveillance and Embodiment: Dispositifs of Capture,” Body and Society (2016, forthcoming) and Smith, Opening the Black Box.
[32] danah boyd, It’s Complicated: The Social Lives of Networked Teens (New Haven, CT: Yale University Press, 2014), 5.
[33] Donna Haraway, The Companion Species Manifesto: Dogs, People, and Significant Otherness (Chicago: Prickly Paradigm Press, 2003).
[34] Robert van Krieken, Celebrity Society (New York and London: Routledge, 2012).
[35] See Smith, Opening the Black Box.
[36] At the time of this writing, the footage had been viewed on YouTube over half a million times. “Texting Fail: Woman Falls in Fountain,” posted by CBS, YouTube, Jan. 20, 2011, http://www.youtube.com/watch?v=ZXYY_ep5Nh0.
[37] Jonathan Finn, “Seeing Surveillantly: Surveillance as a Social Practice” in Eyes Everywhere: The Global Growth of Camera Surveillance, eds. Aaron Doyle, Randy Lippert and David Lyon (New York and London: Routledge, 2012), 67-80, 76.
[38] Calvert.
Gavin J.D. Smith (@gavin_jd_smith) is a Senior Lecturer in the ANU’s Research School of Social Sciences. His research explores the social drivers and embodying impacts of mass sensor-driven surveillance, datafication processes, and data sharing practices. He is interested in the modes of labour concomitant on relations of watching and being watched. He is an editor of the open access journal, Surveillance & Society, and is on the SAGE Sociology Video Collection Editorial Advisory Board. His recent book, Opening the Black Box: The Work of Watching (2015, Routledge) provides an ethnographic account of the culture of CCTV operation. His work appears in top-ranking journals such as Body & Society, Critical Public Health, Theoretical Criminology, Health Sociology Review, The British Journal of Criminology, and Urban Studies.
Reader Comments